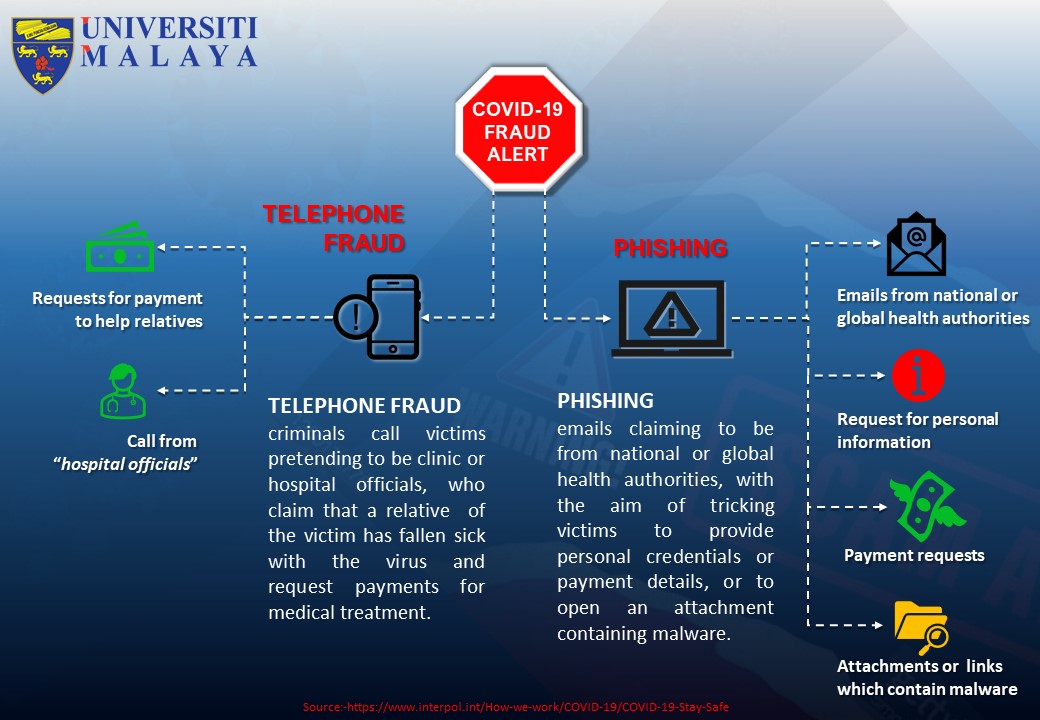
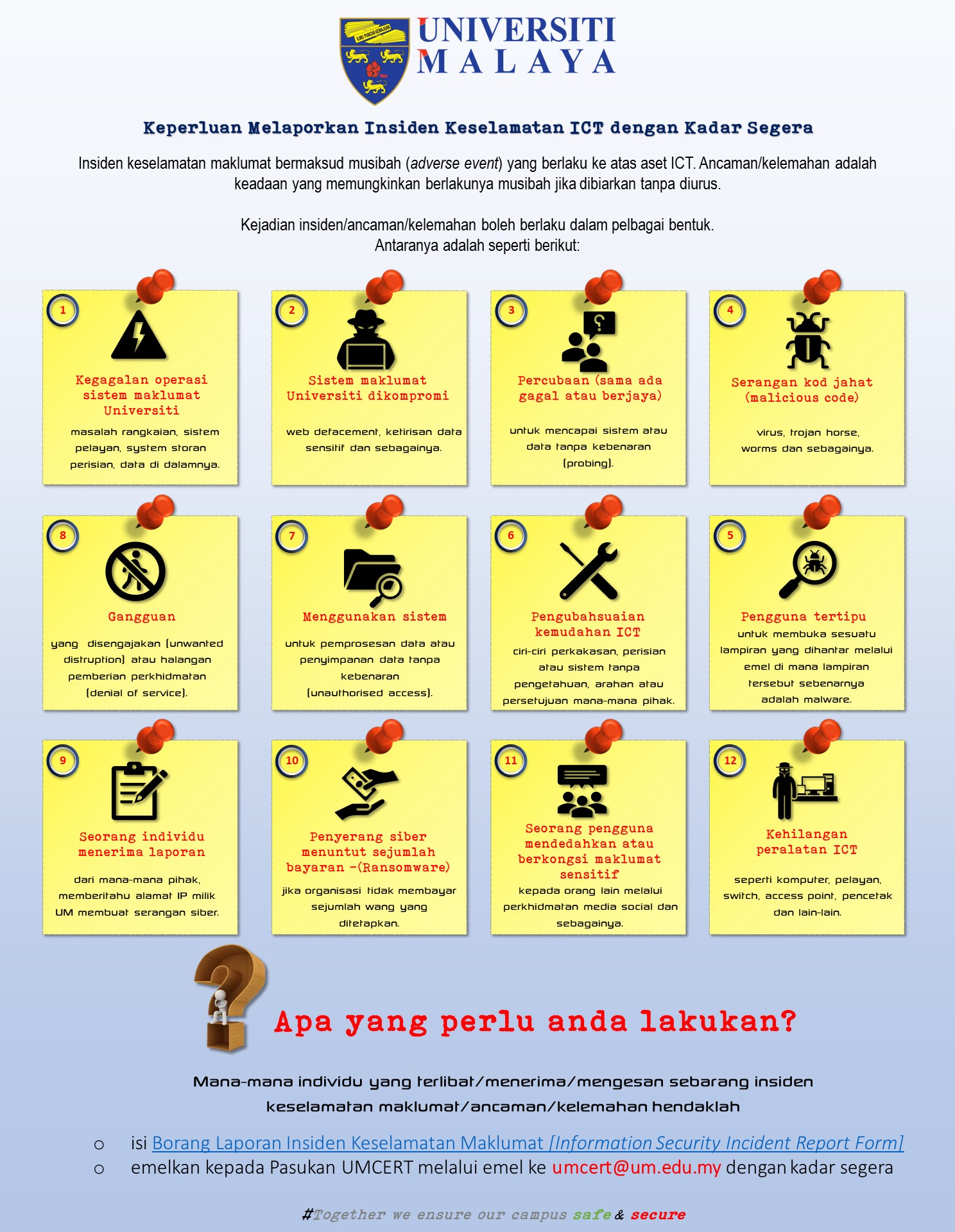
Safety Tips
Safety First


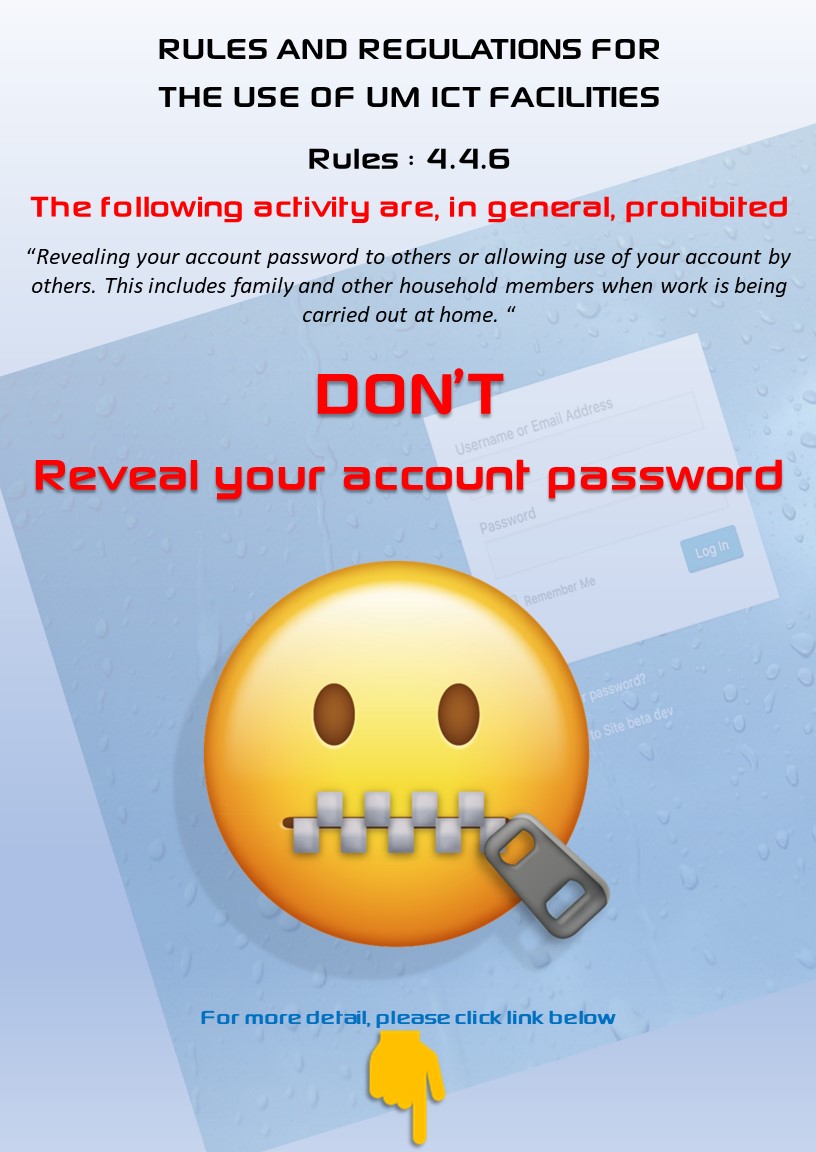
- Never share your password with anyone. Guard your password just as you guard your bank card PIN
- Never say “yes” when your browser asks you if you’d like to save your password.
- How do I clear my browser’s cache memory?
- Never write your password down.
- Never send your password in email, even if the request looks official.
- Fun ways to create a Strong & Memorable password
- Change your password often. Guide on how to change your UMmail password
- Never Give Out Your Password. Poster Don't Give Password
![]()
- If you suspect your UMmail account has been hacked or just want to make sure it hasn’t, please regularly check your UMMail Last Account Activity record.
- Click here for more information.

- To know whether your computer has the basic security features or not, it is advisable for you to audit your pc.
- Download Microsoft WindowsSecurity Audit Checklist For PC
- - How to download Microsoft Windows Security Audit Checklist?
- How to fill Microsoft Windows Security Audit Checklist? - If you need help, PTM ICT Security Team can provide you & your PTJ with PC Security Audit Services session to assess pc security at your departmental level. Email to ICT Security for more information.
- Keep your computer updated with the latest anti-virus and anti-spyware software, and be sure to use a good firewall.
- You need at least 3 components to ensure proper PC security. Click here for more information
- Get anti-virus software from PTM(Only for UM computers - UM staff)– To make a request, go to UM Helpdesk. Click here
- Never open an email attachment unless you are POSITIVE about the source.
- Do NOT download freeware or shareware unless you know it's from a reputable source

Don't wait until you lose hours or even years of work in a single moment:-
- Make copies of your important information, documents and data on portable media (CD, DVD-ROM, thumb drives and external hard drives are ideal).
- Store these copies in a separate location.

- Keeping your operating system up to date is critical. Running whatever antivirus you have in your computer is NOT enough. You can configure your computer to automatically seek out updates.
- - How to manually check for windows 10 updates
- How to manually check for windows 8 & 8.1 updates
- How to manually check for windows 7 updates

- Malware, or malicious software, is hostile, intrusive, or annoying code that includes viruses, spyware, adware, worms, trojan, horses, and other unwanted programs.
- Malware spreads rapidly and by many different ways: for example,e-mail attachments;infected document files; Web sites that contain hostile code that can infect your computer through vulnerable browsers; and unprotected file shares.
- To get the most benefit from your antivirus software ensures it is updated regularly and is operating as intended.
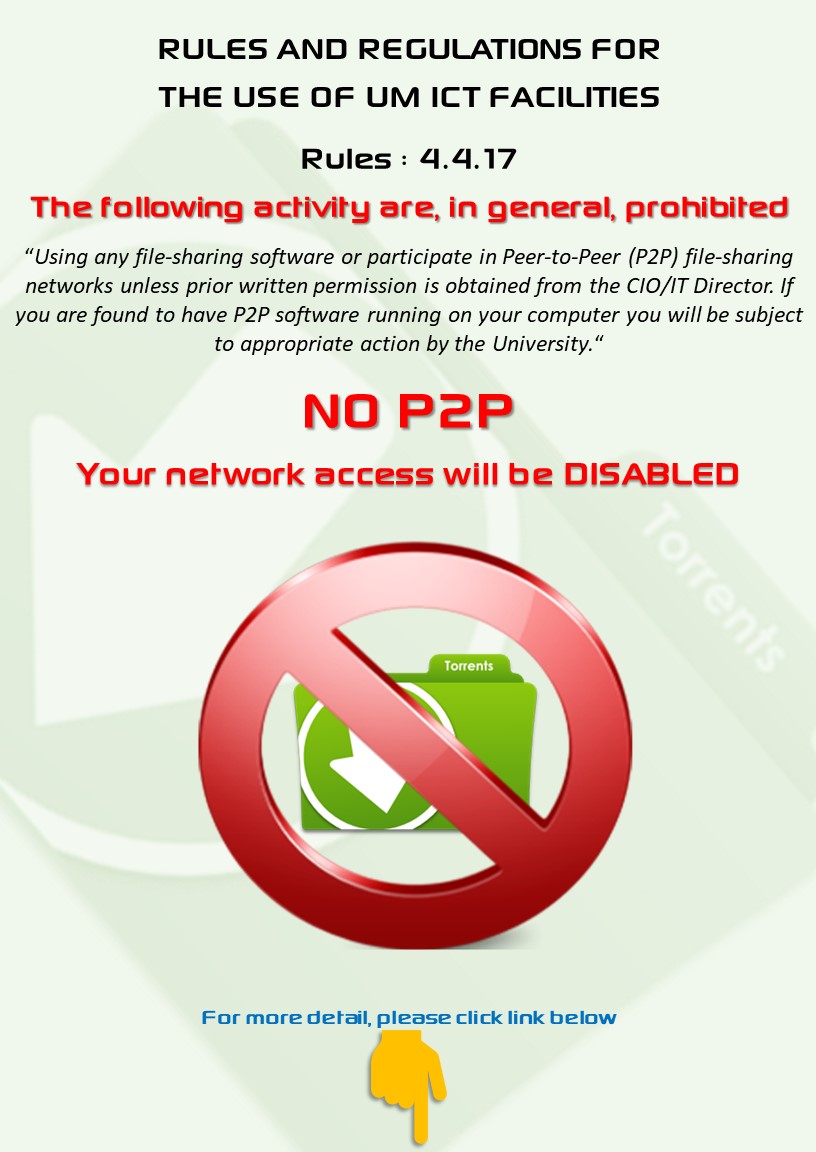
- Be cautious about peer-to-peer sharing networks
- The goal of a phishing scam is to steal your valuable personal data, such as credit card numbers, passwords, account data, and other information.
- If you think you've received a phishing e-mail message, do not respond to it.
Be careful when using Social Networking Websites such as Facebook, Twitter & MySpace.
- Limit the amount of personal info you post
- Customize Privacy Option settings & try to limit access
- Beware of fake pages : these are the sites built by those whose main objective is to steal identity for unlawful financial gains.
 |
 |
 |
| For more detail, please click RULES AND REGULATIONS FOR THE USE OF ICT FACILITIES | ||
 |
 |
 |
| For more detail, please click RULES AND REGULATIONS FOR THE USE OF ICT FACILITIES | ||
 |
 |
 |
| For more detail, please click RULES AND REGULATIONS FOR THE USE OF ICT FACILITIES | ||
 |
 |
 |
| For more detail, please click RULES AND REGULATIONS FOR THE USE OF ICT FACILITIES | ||
 |
 |
 |
| For more detail, please click RULES AND REGULATIONS FOR THE USE OF ICT FACILITIES | ||
 |
||
| For more detail, please click RULES AND REGULATIONS FOR THE USE OF ICT FACILITIES | ||
| Versi Bahasa Malaysia | English Version |
 |
|
|
|
|
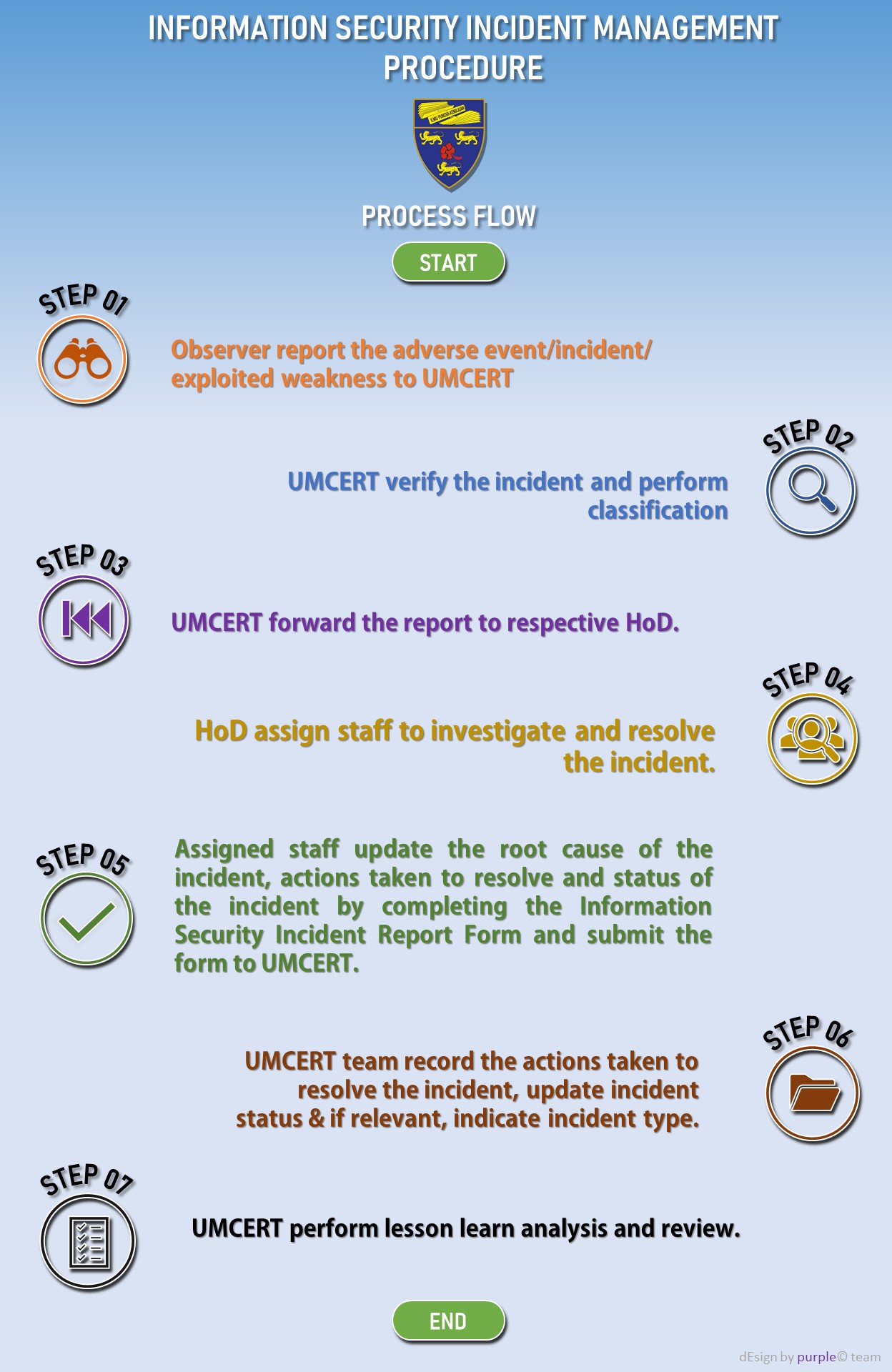
| Untuk keterangan lanjut,sila klik PROSEDUR PENGURUSAN INSIDEN KESELAMATAN MAKLUMAT | For more detail, please click INFORMATION SECURITY INCIDENT MANAGEMENT PROCEDURE |
| Versi Bahasa Malaysia | English Version |
|
|
|
|
Untuk lebih terperinci, sila klik DASAR KESELAMATAN ICT UM |
For more detail, please click UM ICT SECURITY POLICY |
| Versi Bahasa Malaysia | English Version |
 |
 |
|
Untuk lebih terperinci, sila klik |
For more detail, please click |